How do I enable DKIM signing and configure primary and additional domain records?
DomainKeys Identified Mail (DKIM) is an open protocol for protecting email users against email address identity theft and email message content tampering.
DKIM works by providing positive identification of the signer’s identity along with an encrypted “hash” of the message content.
To configure and use DKIM: The system administrator creates a private/public key pair for the server and publishes the public key in the domain’s domain name server. Using the private key, the sending server creates a signature for each outgoing message. The resulting signature data is stored in a “DKIM-Signature” header within the message. The receiving server obtains the signature from the “DKIM-Signature” header, uses DNS to lookup the public key and policy.
In order for a message to be signed, it must meet the criteria designated under the Define which messages are eligible for signing button and be received by MDaemon for delivery on an authenticated session. There is also a Content Filter action, "Sign with DKIM selector..." that you can use to cause messages to be signed.
If the incoming SMTP session does not authenticate with MDaemon, the message will not be signed.
- Select Security
- Select Security Settings
- Expand Sender Authentication
- Select DKIM Signing

- Check Sign eligible outbound messages using DKIM

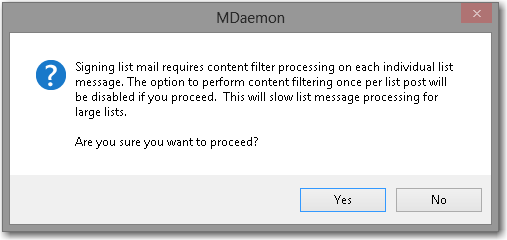
- Check ...sign mailing list messages also (optional).

This will sign every message for all mailing list users, processing times are likely to increase for large lists.
- Either enter a new selector or use the default selector, MDaemon.

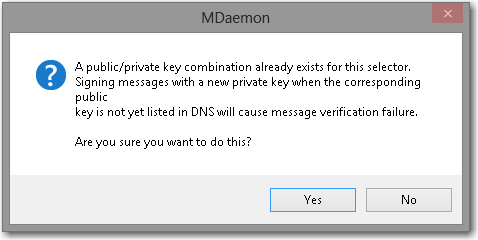
- Click Create new public and private keys.

- Select Yes to have MDaemon generate keys used to create your published DKIM record.
MDeamon creates the dns_readme.txt file in the \MDaemon\Pem\MDaemon\ directory and opens the file onscreen.
In the DNS server, create a TXT record called MDaemon._domainkey.domain.com
- Where MDaemon is the selector name and domain.com is your MDaemon domain name.

The highlighted public key should be entered inside the MDaemon._domainkey.domain.com TXT record and published in the domain's DNS provider.

DKIM Signing with Multiple Domains
MDaemon can be configured to sign messages based on certain criteria, such as choosing a specific DKIM selector and/or domain to sign the message. This is useful if there are multiple domains that are configured in MDaemon. The same selector can be used to sign messages from multiple domains. However, for best results, addresses and/or domains should be defined to sign messages as their domain, regardless of the selector. Not doing so can result in invalid or undesired DKIM verification results.
Follow the steps below to sign messages using a separate selector and/or domain.
- Click the Define which messages are eligible for signing and review the following information to create DKIM signing rules.
- The syntax for entries here are as follows:
<HEADER> <HEADER VALUE> <SELECTOR> <DOMAIN>- Selector and Domain values are optional.
- The syntax for entries here are as follows:
-
- ? and * Wildcards are allowed
- For example, to sign messages from company1.test using the MDaemon1 selector and the company1.test domain, enter the following:
From *@company1.test s=MDaemon1 d=company1.test
- Any header value can be used here (To, Reply-To, Sender, etc..).
- Signing mail for another domain using the same selector is acceptable, though the domain should be defined. For example:
From *@company2.test s=MDaemon1 d=company2.test - Other acceptable examples:
- From user01@example.com
- To *@example.com
- Reply-To *@domain123.example.com s=s1024
- Sender *@domain123.example.com s=January05 d=example.com
- Please use one entry per line.
