How can I use From Header Screening to expose spoofed email?
MDaemon versions 20 and above include an updated From Header Modification feature to help expose spoofed messages that are trying to trick users into thinking the email is from a legitimate source.
Navigate to the From Header Screening menu:
- Select Security
- Select Security Manager
- Expand Screening
- Select From Header Screening
Option 1
The first option will modify the from header and insert the actual email address into the display name.
Example:
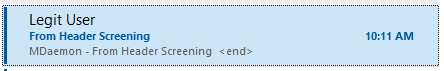
A message is received with the following from headers from a spammer spoofing "Legit User" in the from header.
From: "Legit User" <spammer@spam.com>
To: "User01" <user01@company.test>
Subject: From Header Screening
For this example, Outlook's Message List view shows the display-name only when it exists. The display name is the text in between the quotes in the header. The spammer@spam.com address is not displayed.
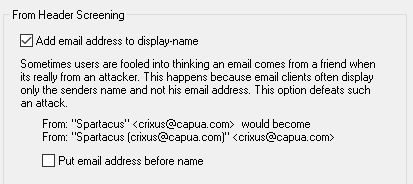
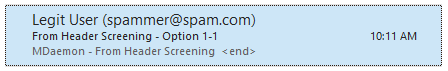
When Add email address to display-name is enabled, the from header above will be modified into the header below.
From: "Legit User (spammer@spam.com)" <spammer@spam.com>
An alternate option is to select Put email address before name is selected to insert the address to the beginning of the header and place the display name in the parenthesis.
FROM: "spammer@spam.com (Legit User)" <spammer@spam.com>
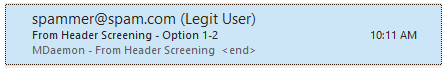
Option 2
With Replace mismatched email address in display-names with real ones is selected, MDaemon compares the address in the display-name against the actual address. If a spammer inserts a legitimate address in the display-name section of the from header to disguise/spoof the spammers actual address, MDaemon will remove the address in the display name and insert the actual address.
Example:
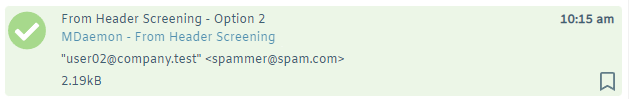
A message arrives with the spammer@spam.com spoofing user02@company.test.
From: "user02@company.test" <spammer@spam.com>
To: "User01" <user01@company.test>
Subject: From Header Screening
Using Webmail for this example, the above headers will display the message as follows.
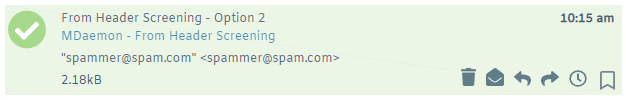
With Replace mismatched email address in display-names with real ones selected, the message would appear as below.
(Optional) Select Do not apply these features to authenticated messages to prevent authenticated sessions from having the from header modified.
Keep in mind when this option is checked, if an account is compromised, an entity submitting spam as this user can still disguise the actual email address behind the display-name.
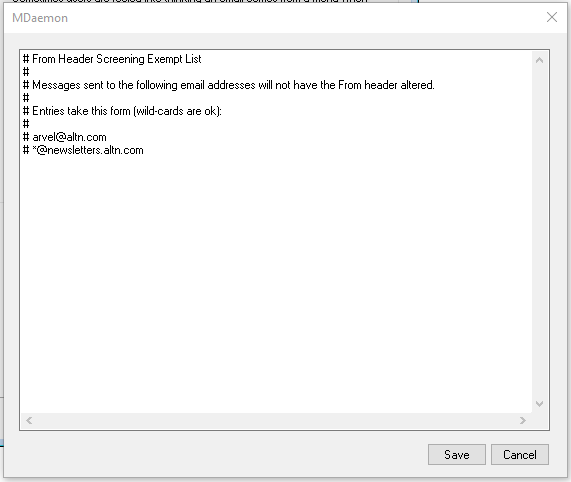
Click Exempt List to bring up a window to enter addresses messages are addressed To that should bypass the From Header Screening options.