Using MDaemon's IP Shield to prevent unauthorized SMTP sessions
New installations of MDaemon will have the IP Shield feature will be enabled by default.
Private IPv4/IPv6 address ranges are added to the IP Shield list. As a result, connections not on the IP Shield list or do not meet exception requirements will not be able to send messages using MDaemon accounts. Remote users who are not providing authentication will not be able to send messages unless their IP address range is on the IP Shield list.
To view the IP Shield settings, follow these steps in the MDaemon console:
- Click Security
- Click Security Settings
- Select IP Shield
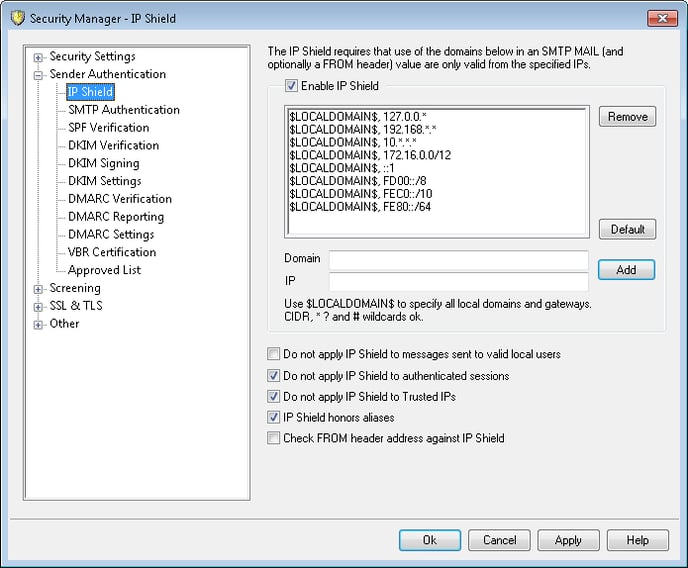
These are the default IPv4 and IPv6 addresses added to the list:
$LOCALDOMAIN$, 10.0.0.0/8
$LOCALDOMAIN$, 172.16.0.0/12
$LOCALDOMAIN$, 192.168.0.0/16
$LOCALDOMAIN$, 127.0.0.1/8
$LOCALDOMAIN$, ::1
$LOCALDOMAIN$, FD00::/8
$LOCALDOMAIN$, FEC0::/10
$LOCALDOMAIN$, FE80::/64
There are three options to bypass the IP Shield
- Do not apply IP Shield to messages sent to valid local users
- Do not apply IP Shield to authenticated sessions (enabled by default)
- Do not apply IP Shield to Trusted IPs (enabled by default)
The IP Shield has the option to honor aliases. This option is enabled by default.
Select the Check FROM header address against IP Shield for the IP Shield to not only look at the SMTP MAIL FROM statement in the SMTP session, but the actual FROM header inside the email itself. This option is disabled by default. While this option is effective in preventing spoofed/invalid messages, this option can cause issues with mailing list mail and should be enabled only if required.
To disable the IP Shield feature, remove the check mark next to Enable IP Shield and then click Ok
